EMV, named after its founders Europay, Mastercard, and Visa, is the international protocol standard for in-store smartcard payment. In December 2020, EMVCo reported 9.89 billion EMV cards in circulation worldwide. Despite the standard’s advertised security, various issues have been previously uncovered, deriving from logical flaws that are hard to spot in EMV’s lengthy and complex specification, running over 2,000 pages.
We have specified a comprehensive model of the EMV protocol, using the Tamarin prover. Using our model, we identified several authentication flaws that lead to critical attacks. We describe next how we demonstrated these attacks in practice and afterwards explain each of the attacks in technical details.
Demonstrating the attacks
To demonstrate the feasibility of the attacks, we developed a proof-of-concept Android application. Our app implements the attacks as man-in-the-middle attacks built on top of a relay attack architecture, using two NFC-enabled phones.
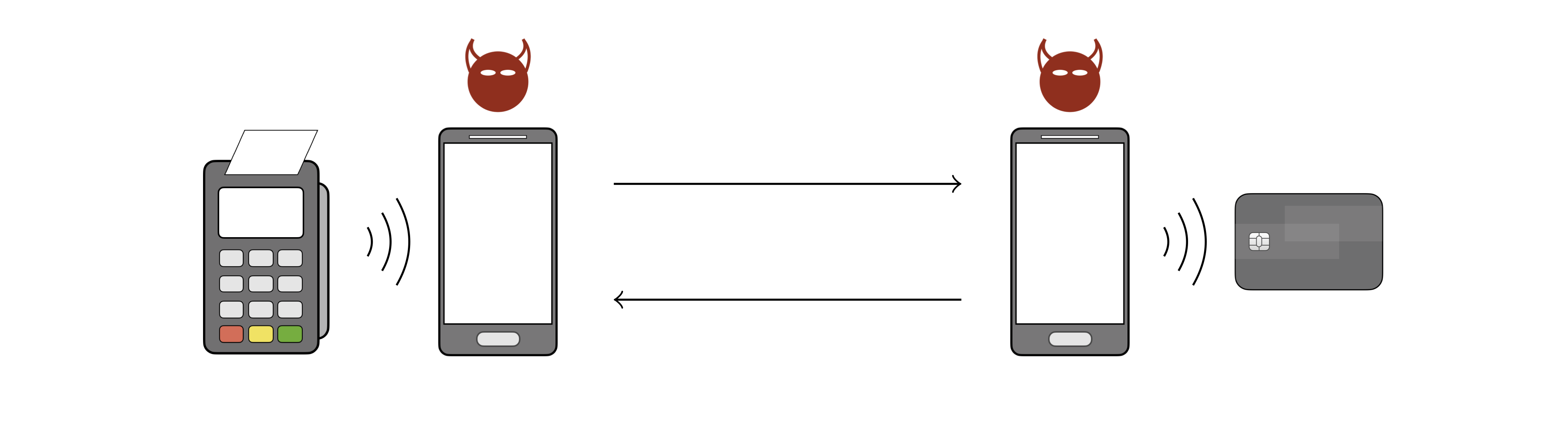
The outermost devices are the payment terminal (on the left) and the victim’s contactless card (on the right). The phone near the payment terminal is the attacker’s card emulator device and the phone near the victim’s card is the attacker’s POS emulator device. The attacker’s devices communicate with each other over WiFi, and with the terminal and the card over NFC.
For the attacks to work, the criminals must have access to the victim’s card, either by stealing it, finding it if lost, or by holding the POS emulator near it if still in the victim’s possession. The attacks work by modifying the terminal’s commands and the card’s responses before delivering them to the corresponding recipient.
Our app does not require root privileges or any hacks to the Android OS. We have used it on Google Pixel, Samsung, and Huawei devices.
PIN bypass for Visa cards
Criminals can complete a purchase over the PIN-required limit with a victim’s Visa contactless card without knowing the card’s PIN. Namely the PIN in your Visa card is useless since it won’t prevent your card from being used for unauthorized, high-value purchases.
In technical details, the attack consists in a modification of the Card Transaction Qualifiers (CTQ, a card-sourced data object), before delivering it to the terminal. The modification instructs the terminal that:
- PIN verification is not required, and
- the cardholder was verified on the consumer’s device (e.g., a smartphone).
We have successfully tested this attack with Visa Credit, Visa Debit, Visa Electron, and V Pay cards, but it may also affect Discover and UnionPay cards. An attack demo for a 200 CHF transaction with a Visa card is given below.
A full report on this attack is given in our paper:
David Basin, Ralf Sasse, and Jorge Toro-Pozo
42nd IEEE Symposium on Security and Privacy (S&P 2021)
[PDF] [BibTex] [Tamarin models] [Best Practical Paper Award]
PIN bypass for Mastercard cards
We have discovered security flaws that lead to two different variants of a PIN bypass for Mastercard/Maestro cards.
Variant 1: Card brand mixup
Criminals can trick a terminal into transacting with a victim’s Mastercard contactless card while believing it to be a Visa card. This card brand mixup attack, in combination with the above PIN bypass for Visa cards, results in a PIN bypass also for Mastercard cards.
In technical details, this attack primarily consists in the replacement of the card’s legitimate Application Identifiers (AIDs) with the Visa AID A0000000031010 to deceive the terminal into activating the Visa kernel. The attacker then simultaneously performs a Visa transaction with the terminal and a Mastercard transaction with the card. In the Visa transaction, the attacker applies the aforementioned attack on Visa.
For this attack to work, the terminal’s authorization request must reach the card-issuing bank. Requirements for this include:
- the terminal does not decline offline even if the card number (PAN) and the AIDs indicate different card brands, and
- the merchant’s acquirer routes the transaction authorization request to a payment network that can process Mastercard cards.
We have successfully tested this attack with Mastercard Credit and Maestro cards, but it may also affect JCB and American Express cards. An attack demo for a 400 CHF transaction with a Maestro card is given below.
A full report on this attack is given in our paper:
David Basin, Ralf Sasse, and Jorge Toro-Pozo
30th USENIX Security Symposium (2021)
[PDF] [BibTex] [Tamarin models]
Variant 2: PIN bypass via authentication failures
In the Mastercard contactless transaction, the payment terminal validates the card offline using a PKI, where the root CA’s PK is looked up from a terminal’s internal list. The index of this root PK in the list is determined from card-supplied data that can be arbitrarily modified. We have observed that if this index is modified to an invalid one (e.g. one that is out of bounds) then the terminal does not perform any PKI checks during the transaction. This flawed failure mode in the protocol makes critical data, whose integrity is only protected offline, vulnerable to adversarial modification. Such critical data includes the card’s list of supported methods for cardholder verification.
As a proof-of-concept exploit, we developed a man-in-the-middle attack that modifies this cardholder verification support to make the payment terminal believe that the card (under attack) does not support PIN verification. We realized two versions of this attack:
- downgrade from PIN to (paper) signature, and
- complete removal of the cardholder verification support.
We have successfully tested both versions of the attack with Mastercard and Maestro cards, in several real-world payment terminals. An attack demo for a 500 CHF transaction with a Maestro card is given below, where the cardholder verification has been downgraded from PIN to signature.
A full report on this attack is given in our paper:
David Basin, Patrick Schaller, and Jorge Toro-Pozo
32nd USENIX Security Symposium (2023)
[PDF] [BibTex]
Media
Our findings have attracted significant media attention. Below, we list some of the most relevant articles available on the web:
On the attack for Visa
On the attacks for Mastercard
FAQ
What cards are/were affected by these attacks?
We have successfully bypassed the PIN for Visa Credit, Visa Debit, Visa Electron, V Pay, Mastercard Credit, and Maestro cards. Further EMV cards may be affected but we have no proof of this in the wild.
Has there been any response by the affected companies?
We have disclosed the attacks to both Visa and Mastercard. As a result of our successful disclosure process with Mastercard, the payment network has since implemented and rolled out defense mechanisms against the brand mixup attack.
What role did Tamarin play in this research?
Tamarin is a state-of-the-art verification tool. With it, we analysed the full execution flow of an EMV transaction with unboundedly many executions occurring simultaneously in an adversarial environment, where all messages exchanged between the terminal and the card can be read/blocked/injected. The outcome of this analysis was, in various cases, the identification of the novel attacks we focus here, as well as the rediscovery of existing ones. We also used Tamarin to design and verify (under all adversarial conditions explained above) defenses to all attacks.
There have been many attacks on EMV before, what makes these different?
Practical attacks reported before are either conspicuous and thus hard to exploit in practice, or do not seem lucrative for criminals due to being possible for low-value purchases only. Our attacks allow criminals to carry out high-value fraudulent transactions and are performed using an app that looks just like a commercial payment app such as Apple Pay or Google Pay, thus evading detection.
What went wrong? How can such problems be avoided in the future?
Critical data sent by the card during a transaction are not authenticated. Complex systems such as EMV must be analyzed by automated tools, like model checkers. Humans cannot deal with the volume of execution steps and branches a complex system has, and so security breaches are often missed.
Should we protect our cards in a “metal wallet” to prevent them being read remotely?
This might help. Although you still have problems if they are lost or stolen.
What actions should I as a citizen take now to protect myself?
Protection measures recommended by banks apply. Block your card immediately upon realization it is lost or stolen. Check your bank statement regularly, and immediately report to your bank whenever you see an unrecognized transaction. Additionally, whenever you are carrying an EMV contactless card, make sure nobody is holding a device near it against your will. Also, be aware of your back pocket.
Where do I find the Android app?
Nowhere. We do not make it available.
Team
David Basin1, Ralf Sasse1, Patrick Schaller1, and Jorge Toro2
1ETH Zurich, and 2SIX Digital Exchange
Zurich, Switzerland